Advanced Isolation Strategies for 2026
The SaaS industry is at a crossroads. As the worldwide market rockets towards $315 billion in 2026, driven by the adoption of usage-based pricing and AI monetization, founders and architects are faced with a daunting task: how to safely and scalably build multi-tenant systems without compromising performance or undermining data isolation between customers.
This is not a new problem, but it has never been more pressing. A single “noisy neighbor” tenant, one that executes complex queries or hogs resources, can negatively impact the experience of hundreds of other customers sharing the same infrastructure. At the same time, 59% of SaaS businesses believe that usage-based pricing will help them grow revenue, but metered billing systems require accurate and isolated performance data. Get it wrong, and your billing system will be broken; your customers will be unhappy.
This article examines why multi-tenant data isolation is becoming the technical foundation of successful SaaS businesses, why the move towards metered billing is causing architectural headaches, and what approaches, ranging from database partitioning to containerized workload isolation, are proving successful in the field in 2026.
The Economics of Multi-Tenancy: Why Isolation Became Non-Negotiable
The multi-tenant model has always been the profit driver for SaaS. One app instance, shared resources, economies of scale. This is where the margin advantage came from, making SaaS an attractive investment opportunity for entrepreneurs and investors alike.
However, with shared resources comes a fundamental trade-off: fairness under load. When multiple tenants share resources like CPU, memory, I/O, and database connections, predictability goes out the window. When a customer runs a bulk data import during peak hours, it can saturate available I/O bandwidth, causing transactional queries for other customers to time out. When an inefficient report query maxes out database CPU, it leaves no resources for real-time API calls. This problem, known as the “noisy neighbor problem,” has become the hallmark performance issue of 2026.
The problem is compounded by the fact that usage-based pricing makes isolation a hard business problem, not just a technical one. If you charge customers per API call, per data point processed, or per feature usage, you need isolation. Otherwise, a resource spike from customer A will increase the usage reported by customer B. Revenue integrity is at stake.
The market is reacting by embracing hybrid pricing structures—46% of SaaS businesses now offer base pricing alongside usage fees—and anticipating that usage data will drive revenue growth in ways that seat-based pricing simply couldn’t. Businesses such as Stripe, Twilio, and Snowflake, which adopted usage pricing early, have experienced rapid growth precisely because customers trust their usage data. And that’s because of isolation.
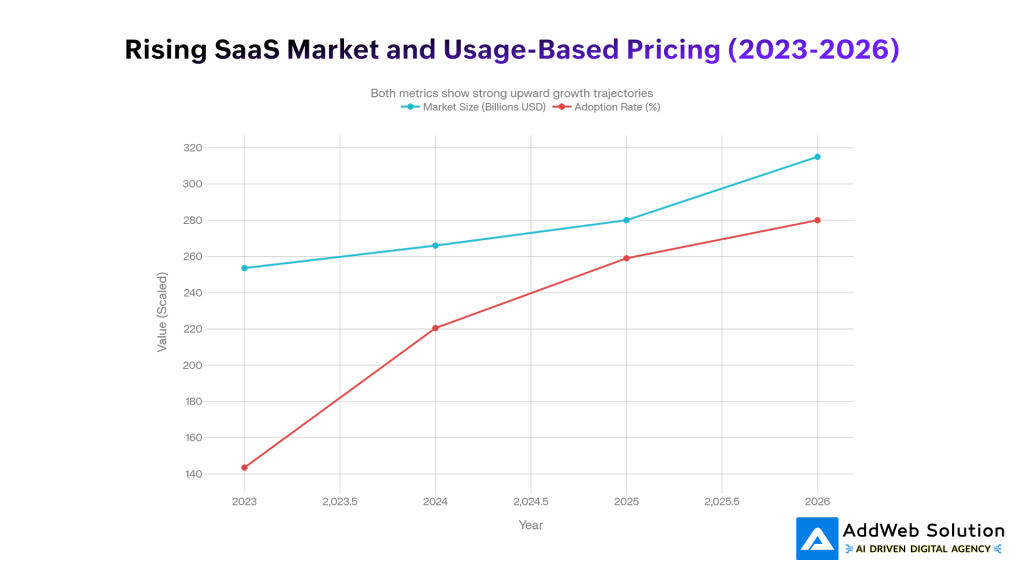
SaaS Market Growth and Usage-Based Pricing Adoption (2023-2026)
The above graph represents the explosive relationship: as the SaaS market grew from $253.58 billion to a forecasted $315 billion between 2023 and 2026, usage-based pricing adoption increased from 41% to 80%. This is no accident. Customers require flexibility; suppliers require dynamic revenue streams; and both require architectural reliability to make it happen.
Why Usage-Based Pricing Requires Improved Isolation
Usage-based pricing, also known as metered pricing or consumption pricing, turns the SaaS business model on its head. Rather than charging per seat or per tier, suppliers charge based on actual consumption: API calls, documents created, storage used, compute resources, or AI tokens processed.
The benefit for customers is self-evident. They only pay for what they use, reducing waste from underutilized seats. The benefit for suppliers is harmony: revenue increases as the customer derives more value. If a customer isn’t using the service, they pay less—and retention increases because they’re not stuck in a contract; they just throttle back.
But metered billing creates operational complexity that traditional licensing never required:
Usage tracking measurement in real-time — Every action must be accurately measured, stored, and invoiced. A usage tracking bug that reports 5% less usage is invisible to the customer but represents a massive loss of revenue. Reporting 1% more usage will lead to churn.
Noise isolation — When a single tenant’s workload peaks, it should not affect the usage data reported to other customers. If tenant A’s batch job uses too much database I/O and slows down tenant B’s API requests, did tenant B’s usage increase? Noise isolation prevents this misattribution.
Fair resource allocation — Smaller customers with lower-tier plans must see consistent performance even when larger customers spike. Otherwise, the pricing structure becomes unfair: smaller customers subsidize larger customers’ resource overages.
Billing variability forecasting — With variable revenue, budgeting becomes more difficult. Enterprises buying SaaS with fixed budgets require revenue caps or minimums. Vendors who only provide usage-based pricing without hybrid plans will lose business.
This is why 73% of SaaS businesses are now actively forecasting variable revenue, and why hybrid models, which incorporate fixed base fees alongside variable fees, have become the new gold standard. The fixed base fee gives predictable revenue and customer stickiness, while the usage-based add-ons give incremental value without shocking customers at the end of the month.
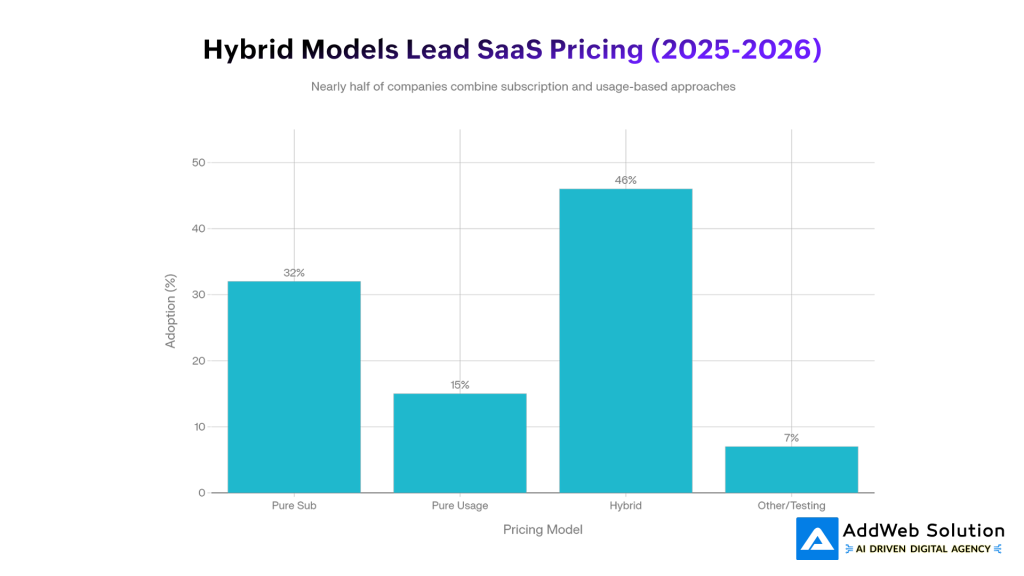
SaaS Pricing Model Adoption Distribution (2025-2026)
The numbers are conclusive: hybrid pricing leads pure subscription by 46% to 32%, while pure usage-based pricing lags far behind at 15%. The reason is simple: customers feel the security of a fixed price, plus the benefit of variable pricing, which together drive business growth without alienating customers.

The Noisy Neighbor Crisis: What Happens When Isolation Fails
The importance of isolation can be appreciated by examining a typical scenario that occurs every day in 2026:
A financial services customer executing month-end reporting at 2 PM launches 50 complex database queries concurrently. These queries lock tables, max out CPU, and flood the query queue. At the same time, a healthcare customer’s real-time patient data API requires response times under 100ms. As the database becomes saturated, the API’s response time increases to 500ms, with some queries timing out altogether.
From the healthcare customer’s side, the SaaS system is “down.” From the vendor’s side, they properly served both tenants; it was simply resource contention that made the other tenant run slower.
However, with metered billing, trouble brews: Did the healthcare customer’s API timeouts constitute “usage”? Did they forget to decrement the failed calls from their bill? Customers will be outraged. Customers will be outraged if they refund failed calls, too. They’ve now incentivized the finance customer to purchase less expensive resources elsewhere during peak times.
Isolation solves this problem. When multi-tenant system architecture properly enforces resource isolation—each tenant’s database connections, query times, and CPU usage are strictly limited—the finance customer’s spike will only impact their own billing and performance, not the healthcare customer’s experience.
The danger of isolation violations was demonstrated in 2025 by CVE-2025-23266, a container escape vulnerability that enabled a malicious container to reach host-level access in multi-tenant Kubernetes clusters. The point: separation of concerns (Kubernetes namespaces) is insufficient. Isolation requires resource boundaries at runtime—separate kernels, resource limits enforced at the hypervisor level, not just the orchestration layer.
Traditional Isolation Techniques: Trade-Offs in 2026
When multi-tenant platforms grow in size, designers are left with four traditional techniques of isolation. Each technique has its own set of trade-offs between the level of isolation, expense, manageability, and scalability.
Strategy 1: Database per Tenant
This is the most bulletproof form of isolation. Each customer is provided with a separate database instance. A customer’s query overload does not affect other customers at all, as they are running on entirely separate resources.
Advantages: Provides maximum isolation, allows independent backups and recovery, easy compliance in regulated sectors, ability to set up customized environments for each tenant.
Disadvantages: Involves prohibitively expensive infrastructure, difficult maintenance (upgrades involve synchronizing changes across dozens or hundreds of databases), poor scalability for handling thousands of tenants, high operational complexity.
Best for: High-security regulated sectors (healthcare, finance), small customer bases (fewer than 50 customers), high-end enterprise customers willing to invest in dedicated infrastructure.
Strategy 2: Schema Per Tenant
The compromise solution: all tenants share a database instance, but each has its own schema (or namespace). Queries from one schema cannot accidentally touch another tenant’s tables.
Advantages: Strong isolation via schema boundaries, less expensive than database-per-tenant, simpler to scale than multiple databases, and allows per-tenant customization.
Disadvantages: More complex than shared schema, difficult to share certain resources (like configuration tables), still susceptible to noisy neighbor problems at the database level (one schema’s resource-intensive query can still hog database CPU resources shared by others).
Best for: Mid-market SaaS with 100-500 tenants, applications requiring a balance of isolation and cost constraints, and applications requiring per-tenant customization.
Strategy 3: Row-Level Security (RLS) and Shared Schema
The most cost-effective approach: one database, one schema, one set of tables. Tenant isolation is implemented at the query level via row-level security. Every table has a tenant_id column, and the database (via PostgreSQL RLS policies, for instance) automatically restricts rows to the tenant.
Advantages: Lowest infrastructure cost, highest scalability (number of tenants: thousands), easiest operational maintenance, takes advantage of database capabilities.
Disadvantages: Highest complexity in application code (every query must include a tenant_id filter; one bug causes data leakage), susceptible to noisy neighbor query resource contention, most stringent auditing requirements (RLS policies must be tested and continuously monitored).
Best for: High-volume SaaS applications with thousands of customers (e.g., analytics front ends, B2C applications), applications where the cost per tenant must be lowest, technically competent teams familiar with advanced database capabilities.
Strategy 4: Partition-Based Isolation
Hybrid strategy: shared database with “smart” horizontal partitioning based on tenant ID. The database engine (PostgreSQL, CockroachDB) allows physical separation of data by tenant, which supports partition pruning and resource policies per partition.
Advantages: Good data isolation at the database level, excellent scalability, easy support for multi-region configurations (one partition per region), reasonable resource allocation with partition quotas.
Disadvantages: Difficult to implement, requires support from database system, moderate operational complexity for partition management.
Best for: Large-scale SaaS applications (thousands to millions of tenants), globally distributed systems, applications requiring isolation and scalability.
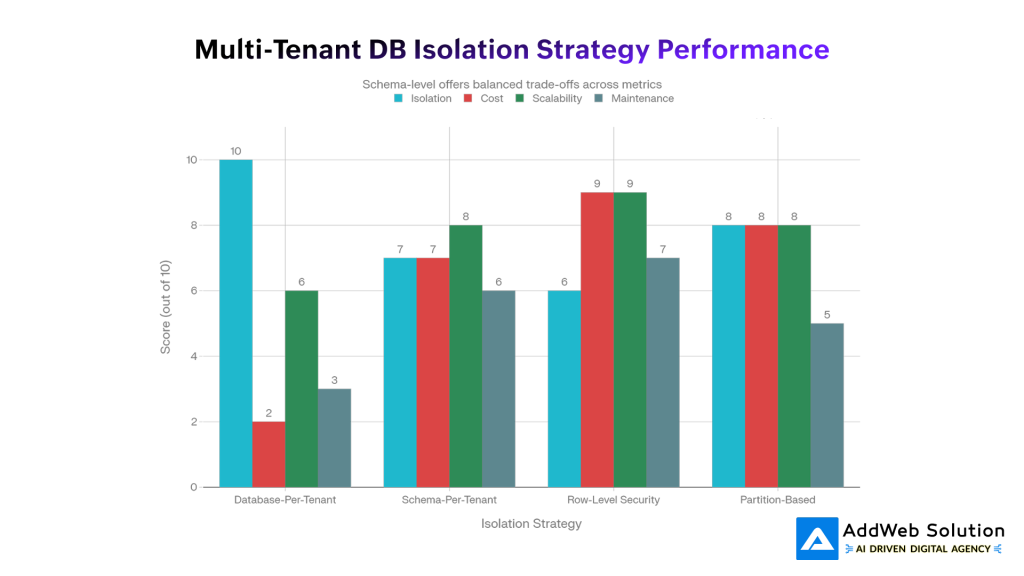
Multi-Tenant Database Isolation Strategies: Trade-off Analysis
The above graph illustrates the trade-offs between isolation, cost, scalability, and manageability. As can be seen, none of the strategies are best in all four aspects. Row-Level Security and Partition-Based strategies are turning out to be the best for 2026 since they provide the maximum possible ROI on infrastructure investment, supporting thousands of tenants with reasonable isolation and manageability.
Beyond the Database: Runtime Isolation and the Kubernetes Problem
Database isolation addresses the issue of data access, but it does not entirely eliminate the noisy neighbor problem. One tenant’s application code can still consume runtime resources such as CPU, memory, and network bandwidth, impacting other tenants’ performance.
This is where containerization and orchestration come into the picture. Kubernetes has become the standard platform for running multi-tenant SaaS in 2026, providing namespace isolation, resource quotas, and network policies. However, Kubernetes namespaces offer logical isolation, not runtime isolation.
The architectural truth: if there are ten tenants’ pods on the same Kubernetes node and the same underlying Linux kernel, a container from one tenant can still escape the isolation barrier by:
- Kernel exploits (privilege escalation)
- Side-channel attacks using shared memory
- Resource exhaustion (out-of-memory crash impacting all co-resident containers)
- GPU memory leaks (in case of shared GPUs for AI applications)
The solution is hardened container runtimes. Solutions such as Kata Containers and Edera Runtime run each container inside a lightweight VM with its own isolated kernel. The performance overhead that made VMs unfeasible in 2015 is no longer an issue—hypervisor overhead is now 5-10%, which is acceptable for most SaaS applications.
In 2026, the isolation stack is:
- Namespaces (logical segregation) – Lowest cost, highest risk.
- Resource quotas + node affinity (Kubernetes segregation) – Medium-level isolation, medium cost.
- Hardened runtimes (VM-based segregation) – Full runtime segregation, acceptable performance hit.
- Separate clusters (cluster-per-tenant) – Maximum segregation, maximum cost.
The majority of SaaS platforms are at tier 2 (resource quotas) or are in the process of moving to tier 3 (hardened runtimes) for their higher-end customers. Tier 4 is typically reserved for niche enterprise customers where the need for segregation outweighs the operational complexity.
How Runtime Segregation is Implemented
The process to avoid noisy neighbors in a Kubernetes cluster:
Resource requests and limits – Set CPU and memory resource requests (what the pod will get) and limits (what the pod cannot go over). When a pod reaches its limit, Kubernetes will automatically remove it, giving the resources back to other pods.
Connection pooling with tenant quotas – Use PgBouncer to limit concurrent database connections per tenant. When a tenant hits its limit, new connections are queued or denied, preventing connection exhaustion.
Query timeouts – Add statement-level timeouts with tenant-level and enterprise-level tiering. Enterprise customers can have 60 seconds per query, and basic customers can have 15 seconds.
Rate limiting on the application layer – Monitor costly operations for each tenant and start queuing requests that exceed the rate limit. When a tenant reaches their request limit, they get a “retry later” response instead of a degraded experience for others.
Monitoring and alerting – Prometheus and Grafana monitoring can track CPU, memory, and database usage for each tenant. When a tenant’s usage exceeds the historical baseline, alerts are triggered for manual or automated scaling actions.
Workload isolation – Offload heavy batch workloads (bulk imports, report processing) to background job queues with tenant-level fairness. Make sure that a tenant’s job does not deprive other tenants of work.
The result: In a properly isolated multi-tenant system, tenant A’s end-of-quarter reporting surge scales resources for tenant A alone. Tenant B’s real-time API requests see no degradation because their resource pool is protected by hard limits.
Laravel’s Role in Supporting Multi-Tenant SaaS
Laravel, the PHP framework, has become the de facto standard for building multi-tenant SaaS in 2026. With 1.5 million websites powered by Laravel globally and 60% market share among PHP frameworks, Laravel is particularly strong in India and Asia-Pacific regions, where rapid SaaS development at scale is critical.
Why Laravel? Because the framework and its ecosystem provide native support for the isolation and metering strategies outlined above.
Multi-Tenancy with stancl/tenancy
The stancl/tenancy package is the market-leading multi-tenancy solution for Laravel. It abstracts away the complexity of tenant identification, database switching, and per-tenant resource management.
Core capabilities:
- Automatic tenancy — Tenant context is bootstrapped automatically. Database connections switch, caches are namespaced, file systems are prefixed—without forcing developers to write tenant-aware code.
- Dual-architecture support — Supports both single-database (shared schema with tenant_id) and multi-database (database-per-tenant) approaches. Developers choose the isolation strategy; the package handles the plumbing.
- Resource syncing — In multi-database setups, share specific resources (like user accounts) across tenant databases. This enables teams to work across multiple tenant-owned projects without duplication.
- Domain routing — Automatically route requests to the correct tenant based on domain or subdomain, enabling customers to use custom domains while sharing a single application.
The tenancy middleware identifies the tenant from the request context (subdomain, domain, or custom identifier), switches the database connection to that tenant’s database or schema, and executes the routes in tenant-isolated context.
Metered Billing with Laravel Cashier and Stripe
Laravel Cashier is the framework’s native integration with Stripe, handling subscriptions, invoicing, and billing. In 2026, Cashier’s metered billing support is critical for implementing usage-based pricing.
Metered billing in Cashier works by:
- Creating a metered subscription — Associate a customer with a Stripe price that measures usage.
- Reporting usage events — As the customer performs billable actions (API calls, data processed), report those events to Stripe.
- Aggregating for billing — At the billing interval (monthly), Stripe aggregates all usage events and bills the customer for consumption.
This integration is straightforward for simple metered models (e.g., “charge per API call”). But Laravel developers building complex hybrid pricing—where some usage metrics have tiered rates, seat-based charges combine with metered API overages, and customers receive monthly credits—often outgrow Cashier and integrate directly with Stripe Billing or move to specialized billing platforms like Chargebee.
Supporting Isolation at the Application Layer
Beyond database and framework tooling, Laravel applications can implement application-level isolation policies:
Tenant-aware query scopes — Use Laravel’s query scopes to automatically filter by tenant_id. Developers can’t accidentally query across tenants.
Rate limiting per tenant — Laravel middleware can enforce request-rate limits per tenant, preventing resource exhaustion.
Tenant-aware caching — Use cache keys prefixed with tenant ID, ensuring cached data is never leaked between tenants.
Audit logging — Log all data access with tenant context, enabling compliance audits and breach detection.
Permission gates — Use Laravel’s authorization gates to validate that a user belongs to a tenant before accessing their resources.
When combined with stancl/tenancy and Stripe billing, Laravel becomes a complete platform for building modern, multi-tenant, metered-billing SaaS applications that scale to thousands of customers.
Selecting Billing Platforms: Stripe, Paddle, and Chargebee in 2026
As usage-based pricing becomes standard, selecting the right billing platform is a critical architectural decision. Three platforms dominate the SaaS billing landscape:
Stripe Billing
Best for: Flexibility-first platforms, complex custom billing logic, global expansion.
- Pricing: 2.9% + $0.30 per transaction
- Metered billing: Advanced usage-based billing with meters, rate cards, and configurable service intervals
- Payment methods: 135+ currencies, 30+ payment methods
- Tax handling: Requires separate integration (Tax Compliance or third-party tools)
- Strengths: Developer-friendly API, extensive customization, no monthly fees
- Limitations: Tax/compliance not included; complex billing logic requires custom implementation
Use case: A SaaS analytics platform charging per API call, per stored metric, and per user. Stripe’s rate cards enable defining different prices for different metric types.
Paddle
Best for: SaaS teams wanting operational simplicity, an all-in-one merchant of record solution.
- Pricing: 5% + $0.50 per transaction
- Model: Merchant of Record (handles payments, taxes, compliance)
- Metered billing: Supported but simpler than Stripe; good for straightforward per-unit consumption
- Strengths: Tax compliance included, built for SaaS, straightforward setup
- Limitations: Less customization than Stripe, higher transaction fees, vendor lock-in
Use case: A SaaS startup in the UK or EU wanting to launch globally without managing VAT/GST compliance. Paddle handles all tax obligations automatically.
Chargebee
Best for: Mature SaaS companies managing complex subscription and hybrid billing scenarios.
- Pricing: Free for first £200k ARR, then 0.75% + payment processor fees
- Model: Subscription management platform (connects to Stripe, PayPal, Braintree)
- Metered billing: Native support for tiered, hybrid, and usage-based with per-tenant customization
- Strengths: Automation (invoicing, dunning, renewals), deep analytics, flexible multi-gateway support
- Limitations: Requires separate payment processor (additional fees); steeper learning curve
Use case: A SaaS company with 500+ paying customers, multiple pricing tiers, usage-based add-ons, and complex billing scenarios (e.g., contracts with annual commitments and monthly overages). Chargebee automates invoice generation, handles failed payment recovery, and provides detailed revenue recognition reporting.
Comparison Table
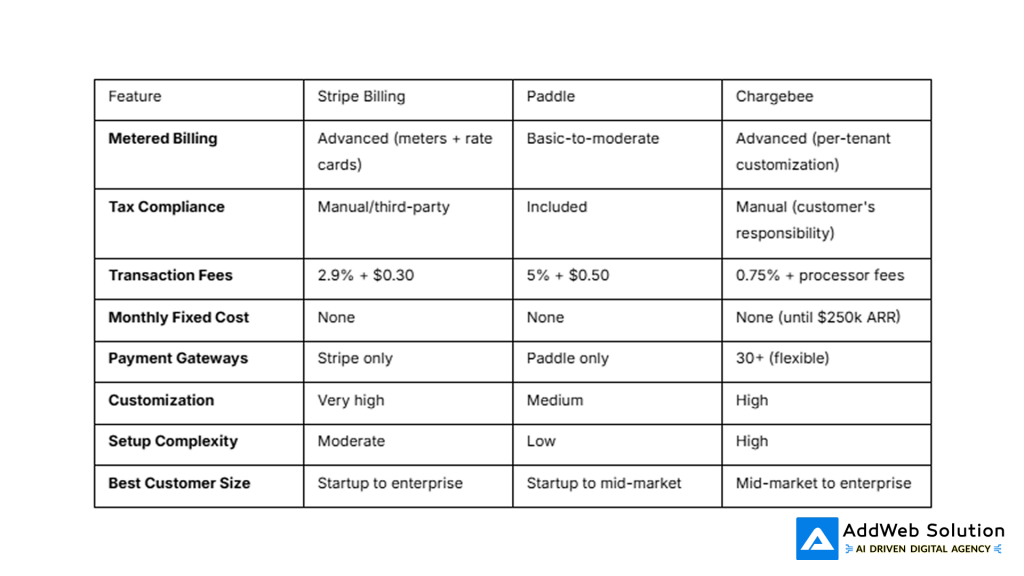
Selection framework:
- Early-stage (< $10k MRR): Paddle for simplicity, or Stripe if you need advanced customization.
- Growth stage ($10k-$100k MRR): Chargebee if you have complex pricing; Stripe if you need maximum flexibility.
- Scale stage ($100k+ MRR): Chargebee with custom negotiations, or Stripe with dedicated integrations.
Market Signals and Revenue Implications
The data in 2026 is unambiguous: usage-based and hybrid pricing models are driving measurable business outcomes.
Growth acceleration: Companies using hybrid models report median revenue growth of 21%, outpacing pure subscription models (15%) and pure usage-based models (17%).
Revenue forecasting maturity: 73% of SaaS companies with usage-based pricing actively forecast variable revenue for financial planning. This sophistication—modeling revenue as a distribution rather than a fixed number—separates mature SaaS companies from startups.
AI monetization boom: 44% of SaaS companies now charge for AI-powered features. Unlike traditional SaaS with economies of scale, AI features have high variable costs (LLM inference, GPU compute). Usage-based pricing is the natural fit: charge customers proportionally for the computational resources you consume serving them.
Regional variation: North America leads in pricing innovation, with 72% of U.S.-based SaaS companies offering usage-based options. Asia-Pacific, particularly India, is rapidly catching up, with Indian SaaS startups prioritizing flexible pricing from inception.
Customer preference: 80% of SaaS customers report that usage-based pricing better aligns with the value they receive. For enterprise buyers, this translates to better deal economics: no more overpaying for seat licenses they won’t use, and transparent cost attribution by business unit.
The business implication is stark: founders and CTOs who bet on multi-tenant architecture, metered billing, and advanced isolation in 2026 are building defensible, high-margin businesses. They can serve small customers cheaply (low infrastructure overhead per tenant) and large customers profitably (metered revenue captures enterprise value). The cost structure is inherently scalable; the revenue model is aligned with customer success.
Building for Isolation: Key Design Decisions in 2026
For teams architecting multi-tenant SaaS platforms in 2026, these decisions will define your technical trajectory:
1. Choose Your Database Isolation Strategy Early
- Small customer count or highly regulated? Database-per-tenant.
- Mid-market with 100-500 customers? Schema-per-tenant balances isolation and cost.
- Thousands of customers, cost-sensitive? Row-level security or partition-based isolation.
This decision is expensive to reverse. Choose wrong, and either your cost structure becomes uncompetitive, or your isolation becomes leaky.
2. Invest in Runtime Resource Isolation from Day One
- Implement Kubernetes resource requests and limits rigorously.
- Monitor tenant-level resource consumption (CPU, memory, I/O).
- Plan for hardened container runtimes (or cluster-per-tenant) as you onboard enterprise customers.
The noisy neighbor problem will surface at ~500-1000 tenants. By then, retrofitting isolation is expensive.
3. Align Your Billing Platform with Your Pricing Model
- Simple usage-based? Stripe Billing is sufficient.
- Complex hybrid with multiple metrics? Chargebee.
- Global expansion with tax burden? Paddle.
Don’t over-engineer with Chargebee if Stripe suffices; don’t under-engineer with Stripe if you need Chargebee’s automation.
4. Make Multi-Tenancy Invisible to Product Teams
Use frameworks like Laravel with stancl/tenancy so developers don’t think about tenants. Tenant isolation should be a solved problem, not a source of bugs.
5. Build Observability for Multi-Tenant Fairness
- Track response times, error rates, and throughput per tenant.
- Alert when one tenant’s performance degrades relative to others.
- Use load testing to validate isolation under stress.
Observability prevents silent data quality issues: usage reporting that’s off by 1-2% per customer.
The 2026 Outlook: Isolation as Competitive Advantage
Multi-tenant SaaS platforms with strong isolation practices have a profound competitive advantage: they can serve vastly larger customer bases at lower per-customer cost than single-tenant competitors, while maintaining the performance quality and data security that modern customers demand.
The companies winning in 2026 are those that treated isolation not as an afterthought or a security feature, but as a core architectural principle. They designed databases for fair resource sharing, implemented runtime controls to prevent noisy neighbors, built comprehensive observability to validate fairness, and aligned their billing platforms to capture the value they deliver.
As usage-based pricing continues its rapid adoption—59% of SaaS companies expect it to drive significant revenue share in 2026—the technical teams that master isolation will be the teams that unlock true value alignment with customers. Revenue will flow toward companies that bill fairly, perform reliably, and scale predictably.
For Laravel developers and architects building SaaS products in India, Asia-Pacific, and globally: the platform, frameworks, and billing infrastructure to support this vision exist. Laravel with stancl/tenancy for multi-tenancy, Stripe or Chargebee for billing, Kubernetes for orchestration, and PostgreSQL with row-level security for databases form a complete, proven stack. The competitive advantage belongs to teams that move quickly to consolidate this stack and scale.
The multi-tenant performance crisis isn’t a crisis for well-architected systems. It’s an opportunity for those ready to build for isolation.
Key Takeaways
✓ Hybrid pricing (base subscription + usage-based charges) is now standard, with 46% adoption and highest growth rates of 21% median revenue growth.
✓ The noisy neighbor problem is real and costly, causing performance unpredictability and billing integrity issues in poorly isolated multi-tenant systems.
✓ Database isolation strategies range from database-per-tenant (maximum isolation, high cost) to row-level security (maximum scale, moderate isolation). Choose based on customer count and security requirements.
✓ Runtime isolation via Kubernetes resource quotas, connection pooling, and hardened container runtimes prevents application-level resource contention.
✓ Laravel with stancl/tenancy and Stripe/Chargebee billing provides a complete, proven platform for multi-tenant SaaS at scale.
✓ 59% of SaaS companies expect usage-based pricing to drive revenue growth in 2026. Isolation is the technical foundation that makes metered billing trustworthy.
✓ Observability is non-negotiable: Monitor isolation effectiveness per tenant, validate fair performance, and catch data quality issues early.

Ready to build next-generation multi-tenant SaaS?

Pooja Upadhyay
Director Of People Operations & Client Relations
Ready to build next-generation multi-tenant SaaS?
The technical foundations are mature, the market demand is clear, and the revenue upside is substantial. Start with database isolation strategy, invest in Kubernetes resource controls from day one, and select a billing platform that grows with your pricing model complexity. The teams that do this well in 2026 will define the SaaS landscape for the next decade.
⁂
- https://www.bettercloud.com/monitor/saas-industry/
- https://www.revenera.com/blog/software-monetization/usage-based-pricing-saas-ai/
- https://neon.com/blog/noisy-neighbor-multitenant
- https://stripe.com/in/resources/more/what-is-metered-billing-heres-how-this-adaptable-billing-model-works
- https://cloud.google.com/blog/products/containers-kubernetes/gke-architectures-for-hosting-saas-applications/
- https://laravel.com/docs/12.x/billing
- https://docs.stripe.com/billing/subscriptions/usage-based/advanced/about
- https://learn.microsoft.com/en-us/azure/architecture/antipatterns/noisy-neighbor/noisy-neighbor